Critical information disclosure on Wappalyzer.com

While performing some online assesment, a critical information disclosure has been found on Wappalyzer.com. The vulnerability has been fixed, this is the full disclosure about the issue.
What's Wappalyzer?
Wappalyzer is a nice swift tool used to identify technologies powering the website you are currently visiting. It has browser extensions both for Chrome and Firefox, you can review the full source code on GitHub.
I'm currently using it on a side project of mine, so I'm visiting their site quite often.
Few weeks ago, Wappalyzer decided to monetize their large database and start selling the dataset. This was paired with a change in their site: a new graphic and new features were added.
Recon never ends
At that time I was reading a very interesting article about SQLi + XXE + File path traversal Deutsche Telekom, explaining how recon never ends. Usually vulnerabilities are triggered by small details, maybe in some test subdomain that no one is maintaining.
I found it very inspiring and I decided to try its suggestions on a live site.
First of all I used SubBrute to find some interesting subdomain. Since nothing showed up, I started using DirBuster.
After some time running, I found something interesting:
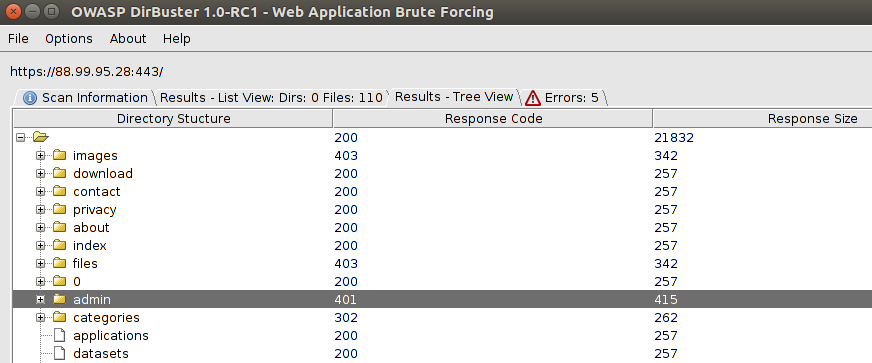
Oh nice! An authentication required! Maybe I can try to bruteforce it for some weak passwords. However, I let it running, just in case there could be something else.

Wait, what? admin requires authentication, but Admin doesn't ?!
Oh boy, this means that we have access to the administrative area?
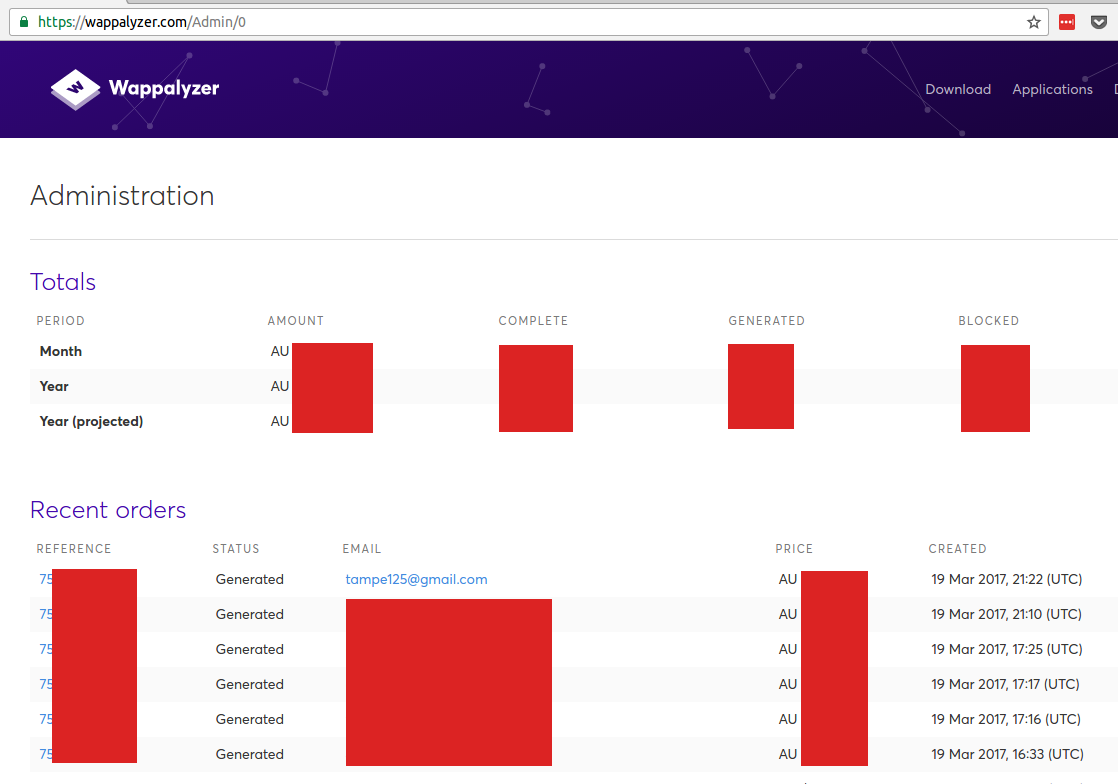
The heavily redacted image shows the most recent orders and their value. The only visible email is my own personal address, used to run some tests.
Links to order details are "protected", too; but switching the case of the folder does the trick.
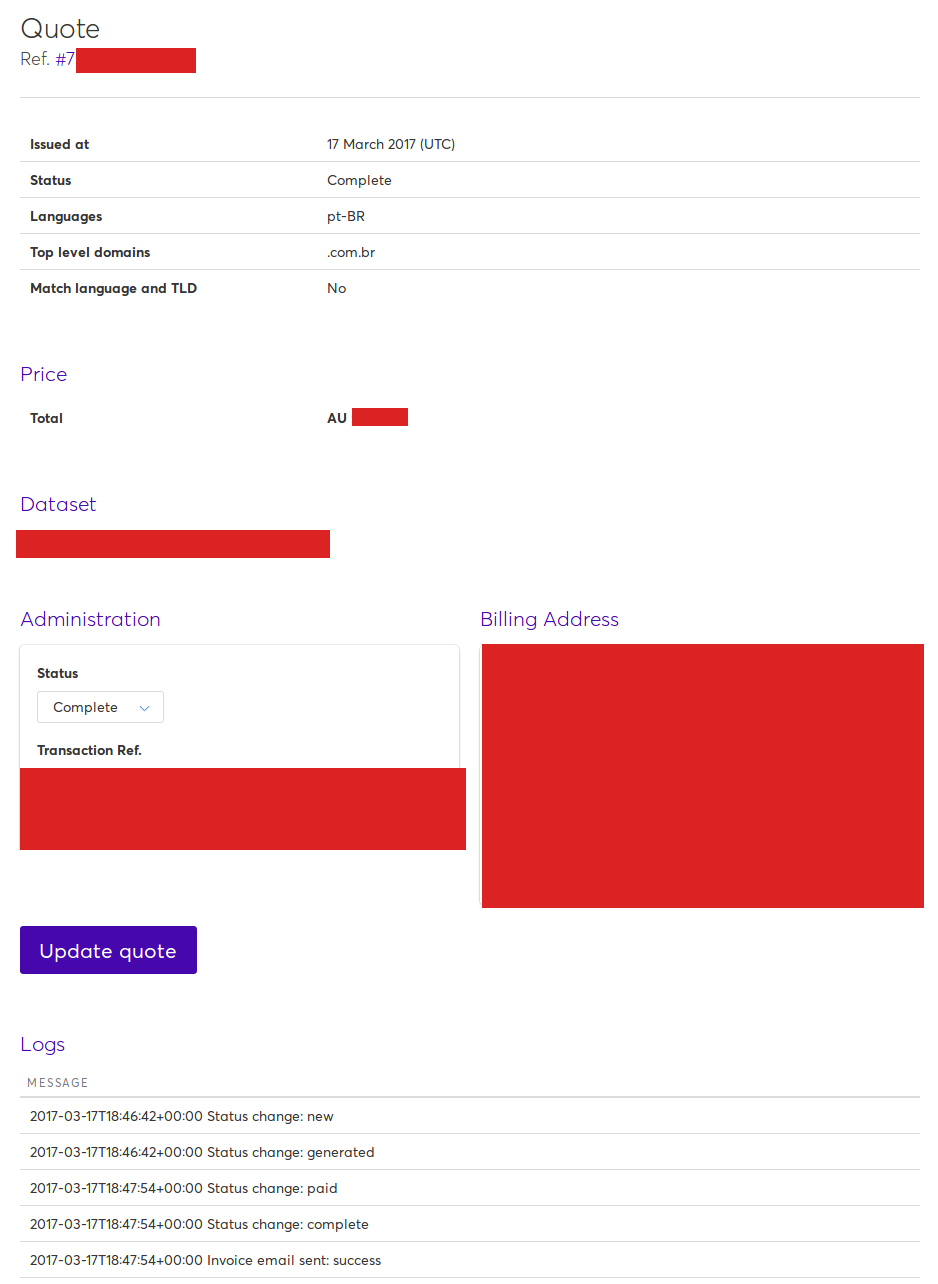
As you can see, in the details page I can change the status of my order. This means that I could just request a quote for the all the available datasets, then log in, change the status to Complete and then download everything free of charge. I didn't actually tried to perform such actions, since it could have disruptive results, but I think it's a plausible scenario.
Conclusions
Once I confirmed the access to the admin area and the disclosure of private information, I immediately got in touch with Wappalyzer owners and they quickly fixed the issue in a couple of hours.
Report timeline
2017-03-20 Initial report to Wappalyzer 2017-03-20 Fix by the vendor 2017-03-24 Full disclosure





 "
"
Comments: